 Law Enforcement Software
Law Enforcement Software
 Law Enforcement Software
Law Enforcement Software
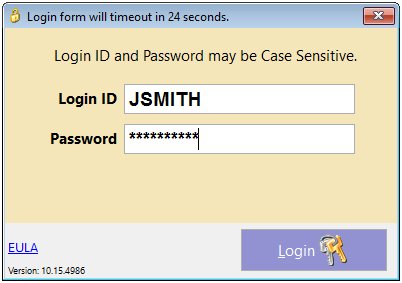
Before you can access any of the modules or features of Crimestar RMS users must first login to the system. This is accomplished via the initial Login screen users must provide a login ID and a password. Both login id's and passwords can be up to 20 characters in length. Login id's can be configured to be case-sensitive if desired. The system can be configured to require that complex passwords be used and passwords can be set to expire after a predefined period of time. See: How to Administer Login Security for more information about complex password requirements, password expirations and inactivity time-out values.
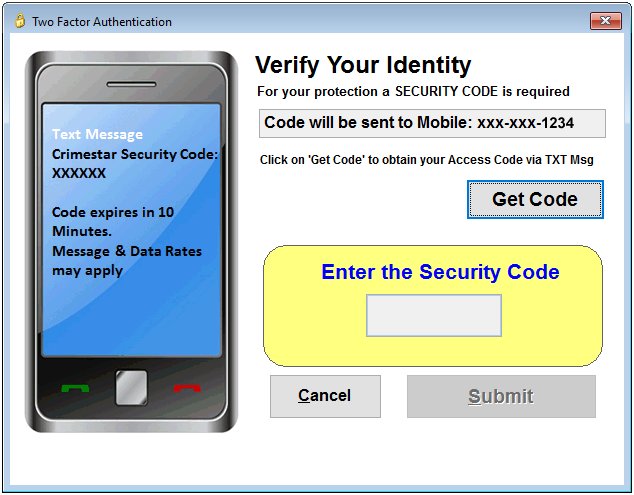
Beyond basic single factor Login ID and Password security the system can be configured to utilize Two Factor Authentication. Two factor Authentication requires that the user both "Know Something" and "Have Something". The something you know is the initial login ID and password as described above. The implementation of the 2nd security factor is accomplished via the user's cell phone (something you have). Two factor Authentication can be implemented on a per-user basis and can be made required by setting that specific option ON and entering the SMS gateway (e-mail) address for the user's cell phone into system security. After the user successfully provides a login id and password they are taken to an additional identity verification form where they request a random 6 digit security code be sent to them. After they receive the Security Code via text message on their cell phone, they enter the Security Code into the identity verification form and proceed into the Crimestar RMS system.
** The delivery of the Security Code via text message requires that the computer workstation where the login is occurring have the appropriate network/internet permissions to access the configured SMTP (email) or SMPP host server so that delivery of the text message to the user can be completed. Do not use two factor authentication unless this connection exists or the user may be locked out of the system until the system administrator changes the users security profile configuration.
See: How to Administer Login Security